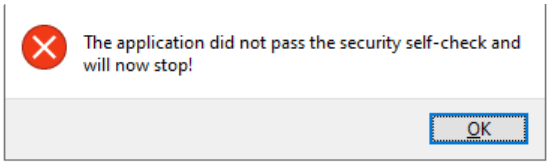
Root Cause
The Windows Authenticode Signature Verification is enabled in the system. The opener.exe cannot pass this verification because it contains the URL of the Server, and every time it is downloaded from a different URL the the .exe file is updated with the new URL. This URL is used to download and open the Thick Client.
Solution
It is required that the Windows Administrators will disable the Windows Authenticode Signature Verification. More information about this can be found in the URL below,
Microsoft Security Advisory 2915720
Note that the Windows Authenticode Signature Verification is not enabled by default in windows systems. This may only be enabled in hardened systems.
We recommend to ask the Windows Administrators to disable this. However, one way to disable it is the following,
Open the Registry of your Environment with Administrative Privileges and delete the following two Registry key values as mentioned below:
- Delete the
HKEY_LOCAL_MACHINE\Software\Microsoft\Cryptography\Wintrust\Config\EnableCertPaddingCheck - Delete the
HKEY_LOCAL_MACHINE\Software\Wow6432Node\Microsoft\Cryptography\Wintrust\Config\EnableCertPadding
